In this guide, we will go through a first technical description of a bitcoin transaction from the creation of the portfolio to the addition of the transaction to the blockchain. Understanding these different stages is essential to then understand the way other crypto-currencies work.
STEP 1 – YOUR BITCOIN PORTFOLIO WILL CREATE YOUR BITCOIN ADDRESS FROM YOUR PRIVATE AND PUBLIC KEYS
The first step is to create a bitcoin address to be able to send and receive bitcoins.
This address is obtained from your public key through a process of a cryptographic hash. To understand how the protocol Bitcoin works, it is essential to have an idea of what represents the hash cryptographic and its functioning. This system is central since it is used at several levels of a bitcoin transaction: To obtain an address, in the bitcoin script and in the “proof of work” performed by minors.
As you can see in the diagram below, the address bitcoin is the outcome of a public key that it the same outcome of the private key.
SCHEMA 1

But before going into the detail of the creation of our keys, it is important to bear in mind that the public key allows you to receive bitcoins, while the private key allows you to spend them. If one compares the payment with bitcoins to the payment by credit card in a store, the public key corresponds to your bank card number, which identifies you and that you can transmit without too many risks, and the private key corresponds to your secret code, which allows you to validate the payment and that you must not disclose.
When you download a portfolio to keep your bitcoins, public and private keys do not appear but they are generated automatically by the portfolio, same for your address bitcoin. You will only see and transfer your address Bitcoin. As shown in the schema 1 above, your address Bitcoin is obtained by applying a double hashing (SHA256 and RIPEMD160) to the public key to obtain what is called the “Public Key hash” (20bytes/160bit). The latter is then encrypted using a Base58check system to obtain a Bitcoin address.
To go further: What is a hashing algorithm? It is a mathematical formula that is applied to a variable number of data (the “input”) in order to transform them into a fixed number of data corresponding to the digital borrows data (“output”). In the case of the algorithm SHA256, the size of the code is always 256 bits. The system of the hash is used in many other areas that the bitcoin to check easily as the initial data (“input”) have not been changed. In fact, two different input may not give an output identical.
For example, if we submit the phrase “Bitcoin is a currency of the future” has the algorithm SHA256 We are going to get a code of 256 bits, which will look like the following code: “0F7becfd3bcd1a82E06663C97176ADD89E7DEE0268of46F94e7e11BC3863E148”. Now if we add a point to the sentence and re-submit to the algorithm, the code obtained will be completely different (even if it will always be 256-bit). In other words, it is impossible to find two different inputs which would give the same output.
It is also important to remember that the hash algorithm only works in one direction and that it is impossible to find the input from the output.

In a very schematic manner, we could compare the hashing mechanism to a press that would reduce one or several elements of different nature (numbers, letters, symbols) and length (input) into a single code of 256 bits (output).
If you want to learn more on this concept, you can make on our article cryptographic hash – The guide to understanding everything.
STEP 2 – YOUR PORTFOLIO WILL THEN CREATE A TRANSACTION BY COMBINING THE INFORMATION INCLUDED IN THE PREVIOUS TRANSACTION (THE ONE YOU HAVE RECEIVED) WITH THOSE OF YOUR RECIPIENT
Imagine a transaction where Alice wants to transfer a bitcoin to Bob. At this stage, Alice and Bob both have a Portfolio and therefore each a set of key private/public and a bitcoin address.
Bob sends to Alice his public key encoded in the form of an address Bitcoin. This address Bitcoin can be transmitted to anyone by any means, either by mail or by QR code.
Upon receipt, Alice (or rather her portfolio) will include the information of this address in the transaction that it will create so that Bob can then prove with its private key that the transaction was well intended.
As shown in schema 2 below, the transactions are linked to each other in the blockchain. The output of a transaction, which included the amount that Alice wants to transfer to Bob and the address information of Bob (in the PubkeyScript) is included in the input to the next transaction.
And it is logical because a bitcoin is, in fact, a right to spend which can be activated with a private key. It is therefore always advisable to keep your private key security because losing a private key, is to lose the unique evidence that you have the right to spend a bitcoin, or rather the output of the transaction that has been created for you by using a lock (the signature script) that only your private key can open.

It is important to note that your portfolio has the ability to combine the amount of several transactions that you have received in the past in order to send the exact amount you want to send.
To go further – in practice, the portfolio of Alice re-transform the Bitcoin Address in “Public Key hash” to create its transaction. Remember that this “Public Key Hash” has been initially created by Bob and therefore contains the information of its public key and its private key. This is essential because Bob will use its private key to obtain the payment.
Alice will use Bob’s “Public Key Hash” to create a “Pubkeyscript”. You can understand the “Pubkeyscript” as a lock with a code that you can open only by aligning the 3 or 4 good numbers. This combination is contained in what is called the “Signature Script” which is designed from the private and public keys that Bob will provide for spending (i.e to create a new transaction) the Bitcoins that he will have received from Alice.
Alice will, therefore, constitute a transaction from an existing transaction (version 1) in the following steps:
1 – by using its own private key and public, her portfolio created a “Signature Script” in the input of the transaction version (2) and thus unlocks the output of the transaction Version 1. In other words, the “Signature Script” (the version 2) is the code required by the “PubKey Script” (the version 1), which had been created from her Bitcoin address.
2 – Creation of a new “output” by Alice: she can now include the amount of bitcoin present in the output of the transaction version (1), in the output of the transaction version (2) and close it with the lock “Pubkey Script” created from the Bitcoin Address of Bob. Thus only Bob will be able to open the lock and spend the output, in turn, creating a transaction by following exactly the same process.
3 – The transaction is then sent on the bitcoin network and miner members will determine whether the code used by Alice (her “Signature Script”) allows her to open the lock of the previous output (the “Pubkey script” of the transaction version 1). If this is the case, the transaction will be added to the Blockchain so Bob can access it.
STEP 3 – YOUR PORTFOLIO WILL SEND THE TRANSACTION TO THE OTHER MEMBERS OF THE NETWORK AND IN PARTICULAR TO THE MINERS WHO WILL VERIFY THE VALIDITY OF THE TRANSACTION AND ADD IT TO A BLOCK
The mining of bitcoin is central to the operation of the system. A new block is added to the blockchain every 10 minutes.
For each block the Minors:
– Verify if the transactions sent on the network are correct,
– add it to a block,
– calculate the hashing of the “header” of this block by realizing the “Proof of work”
– if it is accepted by the rest of the network, it is added to the blockchain,
– the minor obtains the reward that corresponds (coinbase and fees added to each transactions).
The steps are the following:
1. Verification of the validity of the transactions he receives and gathering of these transactions into the same lot (“memory pool”) until there are enough to add them in a block. These checks are intended to determine if the transactions have been constituted in accordance with the rules of the Bitcoin Protocol, such as the existence of an output sufficient to constitute the transaction, an unlocking script corresponding to the locking script, or even more simply that the syntax of the transactions is correct.
The “Memory Pool” must not be mixed with the “Mining pools” which are groups of individual minors which add their computing power to try to win the race for the creation of blocks of transactions.
2. At the same time, the juvenile will constitute a block which is composed of two parts: a “Header” in which are stored information concerning the block in constitution and a “Body”, including all the transactions of the block on the form of a “Merkle tree” (literally a tree of Merkle”). To understand how the blockchain is organised, it is important to understand each of its compostantes described in the “header” and the “body” of each block:
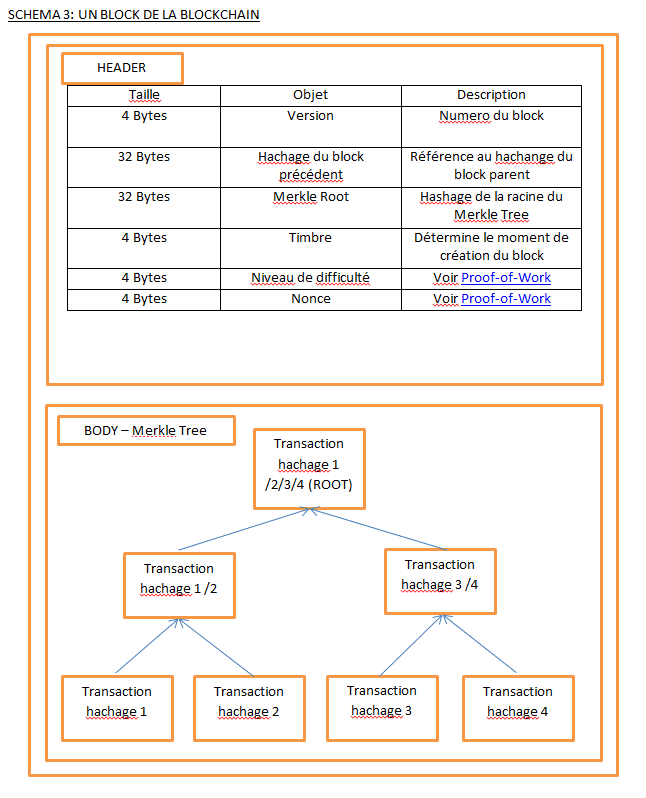
MERKLE TREE: The purpose of a Merkle Tree is to structure data in order to access it more easily and to check its veracity faster. As you would have understood, the name comes from the fact that this method organizes the data by grouping them by two, thus giving the shape of an inverted tree. The transactions are grouped by two, a hash is then applied to this group. The groups is then submitted to the same process with another group until you obtain a single group (the “Merkle Root”) which hashing is added as a reference in the “Header” of the block.
This organization of transactions within a block allows the minors during the verification of new transactions, to go back very quickly to the last transactions concerned and to verify if there is an output of an amount greater than the amount that must be spent in the new transaction (see diagram above).
STEP 4 THE MINORS VALIDATE THE HASHING OF THE HEADER THROUGH THE “PROOF OF WORK PROCESS” AND COMMUNICATES IT TO THE NETWORK TO CONFIRM THAT HE IS THE FIRST AND CAN ADD IT TO THE BLOCKCHAIN.
As we explain in our article “A simple explanation of proof of work“, in a decentralized network such as those based on a blockchain, the difficulty is to have all members to agree on the order of transactions which must be added. It is the whole question of the Consensus between members of the network. Proof of work is one of the mechanisms that allow the members to reach this agreement while ensuring the security of the network. Everyone must not be able to add blocks to the blockchain and get the reward. the members/minors must first demonstrate their involvement by putting at the disposal of the members of the network the computing capacity of its computer (today a computer is no longer sufficient to undermine the bitcoin, only the farms of minages and mining pools may still participate).
The mechanism of “proof of work” can be explained in terms relatively simple: it is the fact for a participant of the network (in the case of the bitcoin, a minor) to submit to the other members of the network, the result of the calculations he has done. The operations to be carried out are not in themselves complicated but must be carried out such an important number of times that the minor must incur significant computing capacity (CPU). The minor must indeed find a random figure (the “Nonce”). For this, he will try his luck until he finds it. It will apply the hashing algorithm to the same group of data (the hash of the previous block) until it obtains the result that it seeks.
If it is the first to discover the Nonce and to transmit it to the rest of the network, the minor win the right to add the block to the blockchain and get the reward in bitcoins and the fees attached to transactions.
If you enjoyed this article, please do not hesitate to LIKE and SHARE it. You can also add you questions in the comments and we will answer them.
Follow me on Social media


![Ledger Nano S review – The Safe of the futur [2020] Ledger Nano S avis](https://www.blockchains-expert.com/wp-content/uploads/2019/10/Ledger-218x150.jpg)

![Binance review: all you need to know [2020] binance review](https://www.blockchains-expert.com/wp-content/uploads/2019/09/binance-218x150.jpg)













![Kraken review: all you need to know [updated 2020]](https://www.blockchains-expert.com/wp-content/uploads/2020/01/kraken-review-2019-4-780x405-100x70.png)
![Ledger Nano S review – The Safe of the futur [2020] Ledger Nano S avis](https://www.blockchains-expert.com/wp-content/uploads/2019/10/Ledger-100x70.jpg)

![Binance review: all you need to know [2020] binance review](https://www.blockchains-expert.com/wp-content/uploads/2019/09/binance-100x70.jpg)


![local bitcoins review – Read this before using [Full Guide 2020] LocalBitcoin avis](https://www.blockchains-expert.com/wp-content/uploads/2019/05/LocalBitcoins-100x70.jpg)
![Bitcoin Value in Dollar – how to analyze and predict it? [Ultimate guide 2020] Bitcoin gold](https://www.blockchains-expert.com/wp-content/uploads/2019/03/Bitcoin-gold-100x70.jpg)





